Cofense
Cofense is a leading provider of phishing defense solutions for organizations worried about the most popular type of attack today – spear phishing. Cofense’s platform turns employees into a proactive line of defense by enabling them to identify, report and prevent spear phishing and drive-by attacks and malware exploits.
Cofense’s open approach enables easy integration with other security systems to improve an organization’s security decision-making. Cofense users include the defense, manufacturing and energy industries, the financial services industry and healthcare entities. Their customers include more than 1,000 global organizations that have understood that changing user behavior will improve security, enable rapid response to new threats and significantly reduce the risk of a successful attack.
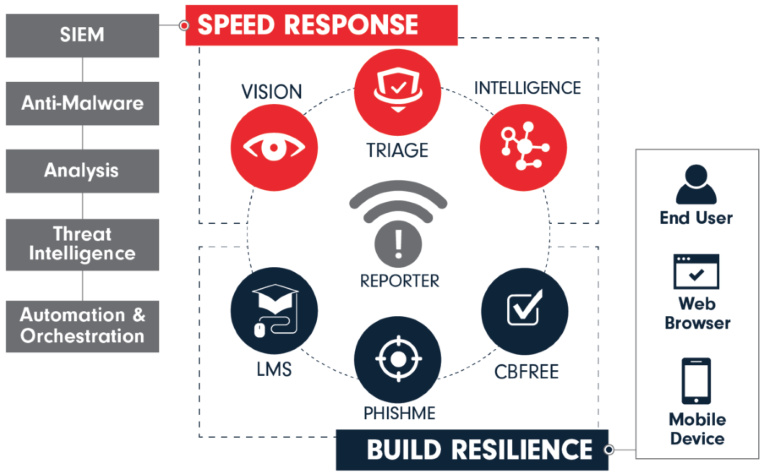
Cofense products in Connect Distribution:
- SECURITY - Phishing Prevension
- MONITORING & MANAGEMENT - Compliance
• Cofense PhishMe Enterprise (normy: SOC 2, GDPR)
Account manager:

Mikołaj Daniłowicz
Account Manager
e-mail: m.danilowicz@connectdistribution.pl
tel.: 22 400 1234
tel. kom.: 784 302 005

